Numerical simulations reveal the formation of singular structures in the polymer stress field of a viscoelastic fluid modeled by the Oldroyd-B equations driven by a simple body force. These singularities emerge exponentially in time at... more
By immersing a compliant yet self-supporting sheet into flowing water, we study a heavy, streamlined, and elastic body interacting with a fluid. We find that above a critical flow velocity a sheet aligned with the flow begins to flap with... more
nature materials | VOL 3 | MAY 2004 | www.nature.com/naturematerials 307 L iquid-crystal elastomers (LCEs) are rubbers whose constituent molecules are orientationally ordered. Their salient feature is strong coupling between the... more
The dynamics of slender filaments or fibers suspended in Stokesian fluids are fundamental to understanding many flows arising in physics, biology and engineering. Such filaments can have aspect ratios of length to radius ranging from a... more
When shaken vertically, a hanging chain displays a startling variety of distinct behaviors. We find experimentally that instabilities occur in tonguelike bands of parameter space, to swinging or rotating pendular motion, or to chaotic... more
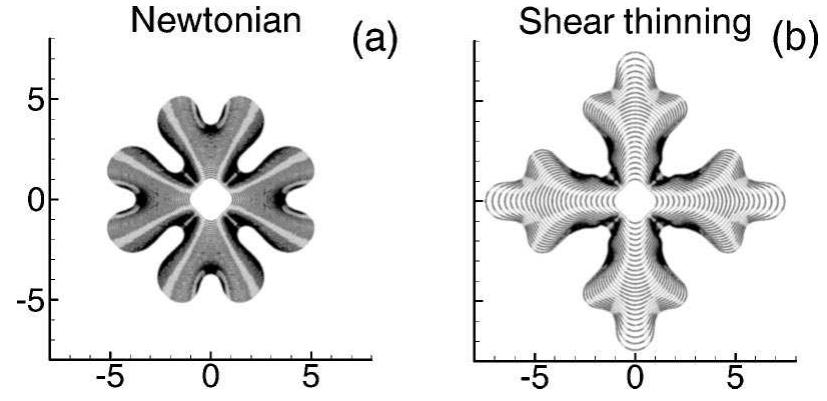
We study theoretically the Saffman-Taylor instability of an air bubble expanding into a non-Newtonian fluid in a Hele-Shaw cell, with the motivation of understanding suppression of tip-splitting and the formation of dendritic structures... more
A mechanism by which smooth initial conditions evolve towards a topological reconfiguration of fluid interfaces is studied in the context of Darcy's law. In the case of thin fluid layers, nonlinear PDEs for the local thickness are derived... more
We study numerically the simplest model of two incompressible, immiscible fluids shearing past one another. The fluids are two-dimensional, inviscid, irrotational, density matched, and separated by a sharp interface under a surface... more
In this paper, we present a meta-cognitive approach for dropping and reconsidering intentions, wherein concurrent actions and results are allowed, in the framework of the time-sensitive and contradiction-tolerant active logic.
In this paper we c o n tend that the ability t o e n g a g e in meta-dialog is necessary for free and exible conversation. Central to the possibility of meta-dialog is the ability to recognize and negotiate the distinction between the use... more
1992 marks the fourth summer of the Institute for Secondary Mathematics and Computer Science Education (IFSMACSE), an NSF-sponsored program for high school teachers held at Kent State University. The program is divided into separate... more
We present a space robotic system capable of capturing a free-flying satellite for the purposes of on-orbit satellite servicing. Currently such operations are carried out either manually or through discrete-event scripted controllers. The... more
This article surveys deformable models, a promising and vigorously researched computer-assisted medical image analysis technique. Among model-based techniques, deformable models offer a unique and powerful approach to image analysis that... more
Animation through the numerical simulation of physicsbased graphics models offers unsurpassed realism, but it can be computationally demanding. Likewise, the search for controllers that enable physics-based models to produce desired... more
A major unsolved problem in computer graphics is the construction and animation of realistic human facial models. Traditionally, facial models have been built painstakingly by manual digitization and animated by ad hoc parametrically... more
We present a novel input device and interface for interactively controlling the animation of graphical human character from a desktop environment. The trackers are embedded in a new physical design, which is both simple yet also provides... more
As a global feature of fingerprints, the orientation field is very important for automatic fingerprint recognition. Many algorithms have been proposed for orientation field estimation, but their results are unsatisfactory, especially for... more
In Active Capture applications, systems that direct human action, the system works with the user to achieve a common goal, for example, taking her picture and recording her name for inclusion on a department web page. The design of Active... more
Characterizing the evolution of Internet topology is important to our understanding of the Internet architecture and its interplay with technical, economic and social forces. A major challenge in obtaining empirical data on topology... more
The Internet AS-level topology is a highly dynamic structure that evolves over time under diverse technical, economical and social forces. Up to now the few efforts on topology visualization have taken only static snapshots of the... more
Traditional routing protocol designs have focused solely on the functionality of the protocols and implicitly assume that all routing update messages received by a router carry valid information. However operational experience suggests... more
The Domain Name System (DNS) is an essential part of the Internet infrastructure and provides fundamental services, such as translating host names into IP addresses for Internet communication. The DNS is vulnerable to a number of... more
Protocol Boosters are functional elements, inserted and deleted from network protocol stacks on an as-needed basis. The Protocol Booster design methodology attempts to improve end-to-end networking performance by adapting protocols to... more
This brief paper outlines our strategies for providing a hardware and software solution to interfacing hosts to high-performance networks. Our prototype implementation connects an IBM RS/6000 to a SONET-based ATM network carrying data at... more
Quality of Service (QoS) guarantees for delay sensitive networked multimedia applications, such as teleoperation, must be application-to-application. We describe a set of services, a service kernel, required at the end points, for... more
The design principle of restricting local autonomy only where necessary for global robustness has led to a scalable Internet. Unfortunately, this scalability and capacity for distributed control has not been achieved in the mechanisms for... more
Z is a softwares ystem designed to provide media-transparent network services on a collection of UNIX®m achines. These services are comprised of file transfer and command execution; Z preserves file ownership on remote transfer,a nd mores... more
We present techniques for analyzing the effect of ''copy-on-write'' page management strategies on the performance of UNIX fork() operations. The analysis techniques are applied on two workstations, the AT&T 3B2/310 TM and the... more
Byzantine and rational behaviors are increasingly recognized as unavoidable realities in today's cooperative services. Yet, how to design BAR-tolerant protocols and rigorously prove them strategy proof remains somewhat of a mystery:... more
We present the first peer-to-peer data streaming application that guarantees predictable throughput and low latency in the BAR (Byzantine/Altruistic/Rational) model, in which nonaltruistic nodes can behave in ways that are self-serving... more
We describe a family of ÐÓ Ò protocols for assigning symmetric keys to Ò processes in a network so that each process can use its assigned keys to communicate securely with every other process. The -th protocol in our protocol family,... more
This paper describes a general approach to constructing cooperative services that span multiple administrative domains. In such environments, protocols must tolerate both Byzantine behaviors when broken, misconfigured, or malicious nodes... more
Pearling is an interactive technique for extracting the centerline and varying thickness of (hand-drawn) curves in images. It works in realtime, is capable of tracing complex curve networks, and supports gesture-driven interactive editing... more
Climate change governance is an emerging topic in the citizen engagement discourse. This is an Expert Group Meeting (EGM) report focused on the socioeconomic impacts of climate change on citizen engagement that reciprocate creative... more
Background: A region of chromosome 16 containing the fat mass/obesity associated 54 gene (FTO) is reproducibly associated with fat mass and body mass index, risk of obesity 55 and adiposity. 56
This paper addresses two major challenges new product development teams face in making a product people want. The first challenge is to frame the design situation based on a real need of a customer. The second, less obvious, challenge is... more
Members of newly formed design teams have different frames – implicit values, goals, and assumptions – they each hold about what problems are important and how they are best addressed. In the early, informal phases of design projects,... more
All learning algorithms attempt to improve the accuracy of a classification system. However, the effectiveness of such a system is dependent on the heuristic used by the learning paradigm to measure performance. This paper demonstrates... more
The main challenge in handwritten character recognition involves the development of a method that can generate descriptions of the handwritten objects in a short period of time. Due to its low computational requirement, fuzzy logic is... more
The main challenge in handwritten character recognition involves the development of a method that can generate descriptions of the handwritten objects in a short period of time. Due to its low computational requirement, fuzzy logic is... more


![FIG. 2. The stability boundary of the straight configuration in the S-U plane as predicted by the model. The scale is such as to ease the comparison with Fig. 9 of [9].](https://figures.academia-assets.com/30894198/figure_002.jpg)